What are EJB’s
Enterprise beans are Java EE components that implement Enterprise JavaBeans (EJB) technology. Enterprise beans run in the EJB container, a runtime environment within the Application Server.
An EJB is essentially a managed component that is created, controlled, and destroyed by the JEE container in which it lives. This control allows the container to control the number of EJBs currently in existence and the resources they are using, such as memory and database connections. Each container will maintain a pool of EJB instances that are ready to be assigned to a client.
When a client no longer needs an EJB, the EJB instance will be returned to the pool and all of its resources will be released. At times of heavy load, even EJB instances that are still in use by clients will be returned to the pool so they can service other clients. When the original client makes another request of its EJB, the container will reconstitute the original EJB instance to service the request. This pooling and recycling of EJB instances means that a few EJB instances, and the resources they use, can be shared between many clients.This maximizes the scalability of the EJB-based application.
There are two different types of EJB that are suited to different purposes:
- Session EJB—A Session EJB is useful for mapping business process flow (or equivalent application concepts). There are two sub-types of Session EJB — stateless and stateful. Session EJBs commonly represent “pure” functionality that is created as it is needed.
- Message-driven EJB—A Message-driven EJB is very similar in concept to a Session EJB, but is only activated when an asynchronous message arrives.
As an application designer, you should choose the most appropriate type of EJB based on the task to be accomplished.
Entity EJB are not part of EJB 3.0 but now are part of JP (Java Persistence) API
Common Uses of EJB’s
So, given all of this, where would you commonly encounter EJBs and in what roles? Well, the following are some examples:
- In a Web-centric application, the EJBs will provide the business logic that sits behind the Web-oriented components, such as servlets and JSPs. If a Web-oriented application requires a high level of scalability or maintainability, use of EJBs can help to deliver this.
- Thick client applications, such as Swing applications, will use EJBs in a similar way to Web-centric applications. To share business logic in a natural way between different types of client applications, EJBs can be used to house that business logic.
- Business-to-business (B2B) e-commerce applications can also take advantage of EJBs. Because B2B e-commerce frequently revolves around the integration of business processes, EJBs provide an ideal place to house the business process logic. They can also provide a link between the Web technologies frequently used to deliver B2B and the business systems behind.
- Enterprise Application Integration (EAI) applications can incorporate EJBs to house processing and mapping between different applications. Again, this is an encapsulation of the business logic that is needed when transferring data between applications (in this case, in-house applications).
When to use Enterprise Beans
You should consider using enterprise beans if your application has any of the following requirements:
- The application must be scalable. To accommodate a growing number of users, you may need to distribute an application’s components across multiple machines. Not only can the enterprise beans of an application run on different machines, but also their location will remain transparent to the clients.
- Transactions must ensure data integrity. Enterprise beans support transactions, the mechanisms that manage the concurrent access of shared objects.
- The application will have a variety of clients. With only a few lines of code, remote clients can easily locate enterprise beans. These clients can be thin, various, and numerous.
Entity Beans
Starting from JEE5 the entity beans have been replaced by Java Persistence API entities. The entities are used to view in an object oriented way o persistent store. In the real world the persistent stores are always relational databases. Typically an entity represents a table in a relational database, and each entity instance corresponds to a row in that table.
Advantages:
- It can run outside of a JEE container.
- Offers a object oriented view of a data base.
- Declaratively transactional support (only if the entity is managed by a Java EE compliant container) Verify This !
- Declaratively security support (only if the entity is managed by a Java EE compliant container) Verify This !
- Transaction aware (only if the entity is managed by a Java EE compliant container) Verify This !
Disadvantages: Dig on this !
Stateless Session Beans
A session bean represents a single client inside the Application Server. To access an application that is deployed on the server, the client invokes the session bean’s methods. The session bean performs work for its client, shielding the client from complexity by executing business tasks inside the server.
As its name suggests, a session bean is similar to an interactive session. A session bean is not shared; it can have only one client, in the same way that an interactive session can have only one user. Like an interactive session, a session bean is not persistent. (That is, its data is not saved to a database.) When the client terminates, its session bean appears to terminate and is no longer associated with the client.
A stateless session bean does not maintain a conversational state with the client. When a client invokes the methods of a stateless bean, the bean’s instance variables may contain a state specific to that client, but only for the duration of the invocation.
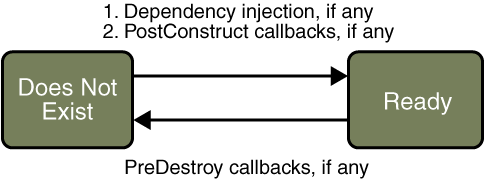
The life cycle of a stateless session bean
Advantages:
- Scalability because stateless session beans can support multiple clients. Typically, an application requires fewer stateless session beans than stateful session beans to support the same number of clients. The instances can be pooled by the container.
- A stateless session bean can implement a web service, but other types of enterprise beans cannot.
- Declaratively transactional support
- Declaratively security support
- Portability
- Transaction aware
Disadvantages:
- Need a JEE container to be executed (the Entity beans can be executed outside a JEE container). Find better than this !
Stateful Session Beans
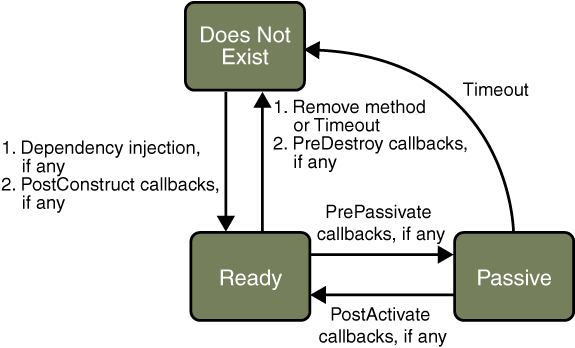
The state of an object consists of the values of its instance variables. In a stateful session bean, the instance variables represent the state of a unique client-bean session. Because the client interacts (“talks”) with its bean, this state is often called the conversational state.
The state is retained for the duration of the client-bean session. If the client removes the bean or terminates, the session ends and the state disappears.
The life cycle of a stateful session bean
Advantages:
- Declaratively transactional support
- Declaratively security support
- Portability
- Transaction aware
Disadvantages:
- Need a JEE container to be executed (the Entity beans can be executed outside a JEE container) Find better than this !
Message Driven Beans
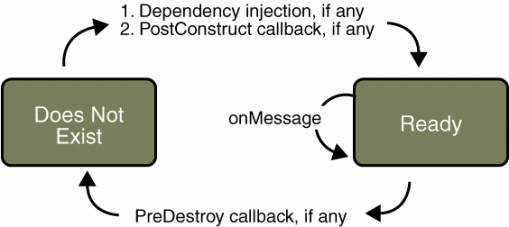
A message-driven bean is an enterprise bean that allows Java EE applications to process messages asynchronously. It normally acts as a JMS message listener, which is similar to an event listener except that it receives JMS messages instead of events. The messages can be sent by any Java EE component (an application client, another enterprise bean, or a web component) or by a JMS application or system that does not use Java EE technology. Message-driven beans can process JMS messages or other kinds of messages.
The Life Cycle of a Message-Driven Bean
Advantages:
- Scalabity; A message-driven bean’s instances retain no data or conversational state for a specific client. The instances can be pooled by the container.
- Simplicity; Unlike a session bean, a message-driven bean has only a bean class.
- Loose coupling between the client and the server; The client have no direct reference to the MDB
- Declaratively transactional support
- Declaratively security support
- Portability
- Transaction aware
- Firewall issues; in some organizations the ports used by JMS can be closed.
- Need a JEE container to be executed (the Entity beans can be executed outside a JEE container). Find better than this !
You must be logged in to post a comment.