Note: This notes were made using the following books: “CISPP Study Guide” and “CISSP for dummies”.
The purpose of access control is to allow authorized users access to appropriate data and deny access to unauthorized users and the mission and purpose of access control is to protect the confidentiality, integrity, and availability of data. Access control is performed by implementing strong technical, physical and administrative measures. Access control protect against threats such as unauthorized access, inappropriate modification of data, loss of confidentiality.
Basic concepts of access control
CIA triad and his opposite (DAD) – see (My) CISSP Notes – Information Security Governance and Risk Management
A subject is an active entity on a data system. Most examples of subjects involve people accessing data files. However, running computer programs are subjects as well. A Dynamic Link Library file or a Perl script that updates database files with new information is also a subject.
An object is any passive data within the system. Objects can range from databases to text files. The important thing remember about objects is that they are passive within the system. They do not manipulate other objects.
Access control systems provide three essential services:
- Authentication – determines whether a subject can log in.
- Authorization – determines what an subject can do.
- Accountability – describes the ability to determine which actions each user performed on a system.
Access control models
Discretionary Access Control (DAC)
Discretionary Access Control (DAC) gives subjects full control of objects they have been given access to, including sharing the objects with other subjects. Subjects are empowered and control their data.
Standard UNIX and Windows operating systems use DAC for filesystems.
- Access control list (ACLs) provides a flexible method for applying discretionary access controls. An ACL lists the specific rights and permissions that are assigned to a subject fora given object.
- Role-Based Access Control (RBAC) is another method for implementing discretionary access controls. RBAC defines how information is accessed on a system based on the role of the subject. A role could be a nurse, a backup administrator, a help desk technician, etc. Subjects are grouped into roles and each defined role has access permissions based upon the role, not the individual.
Major disadvantages of DAC include:
- lack of centralized administration.
- dependence of security-conscious resource owners.
- difficult auditing because of the large volume of log entries that can be generated.
Mandatory Access Control (MAC)
Mandatory Access Control (MAC) is system-enforced access control based on subject’s clearance and object’s labels. Subjects and Objects have clearances and labels, respectively, such as confidential, secret, and top secret.
A subject may access an object only if the subject’s clearance is equal to or greater than the object’s label. Subjects cannot share objects with other subjects who lack the proper clearance, or “write down” objects to a lower classification level (such as from top secret to secret). MAC systems are usually focused on preserving the confidentiality of data.
In MAC, the system determines the access policy.
Common MACs models includes Bell-La Padula, Biba, Clark-Wilson; for more infos about these models please see : (My) CISSP Notes – Security Architecture and Design .
Major disadvantages of MAC control techniques include:
- lack of flexibility.
- difficulty in implementing and programming.
Access control administration
An organization must choose the type of access control model : DAC or MAC. After choosing a model, the organization must select and implement different access control technologies and techniques. What is left to work out is how the organization will administer the access control model. Access control administration comes in two basic flavors: centralized and decentralized.
Centralized access models systems maintains user account information in a central location. Centralized access control systems allow organizations to implement a more consistent, comprehensive security policy, but they may not be practical in large organizations.
Exemples of centralized access control systems and protocols commonly used for authentication of remote users:
- LDAP
- RAS – Remote Access Service servers utilize the Point-to-Point Protocol (PPP) to encapsulate IP packets. PPP incorporates the following three authentication protocols: PAP (Password Authentication Protocol), CHAP (Challenge Handshake Authentication Protocol), EAP (Extensible Authentication Protocol).
- RADIUS – The Remote Authentication Dial In User Service protocol is a third-party authentication system. RADIUS is described in RFCs 2865 and 2866, and uses the User Datagram Protocol (UDP) ports 1812 (authentication) and 1813 (accounting).
- Diameter is RADIUS’ successor, designed to provide an improved Authentication, Authorization, and Accounting (AAA) framework. RADIUS provides limited accountability, and has problems with flexibility, scalability, reliability, and security. Diameter also uses Attribute Value Pairs, but supports many more: while RADIUS uses 8 bits for the AVP field (allowing 256 total possible AVPs), Diameter uses 32 bits for the AVP field (allowing billions of potential AVPs). This makes Diameter more flexible, allowing support for mobile remote users, for example.
- TACACS -The Terminal Access Controller Access Control System is a centralized access control system that requires users to send an ID and static (reusable) password for authentication. TACACS uses UDP port 49 (and may also use TCP).
Decentralized access control allows IT administration to occur closer to the mission and operations of the organization. In decentralized access control, an organization spans multiple locations, and the local sites support and maintain independent systems, access control databases, and data. Decentralized access control is also called distributed access control.
Access control defensive categories and types
Access control is achieved throughout an entire et of control which , identified by purpose, include;
- preventive controls, for reducing risks.
- detective controls, for identifying violations and incidents.
- corrective controls, for remedying violations and incidents.
- deterrent controls, for discouraging violations.
- recovery controls, for restoring systems and informations.
- compensating controls, for providing alternative ways of achieving a task.
These access control types can fall into one of three categories: administrative, technical, or physical.
- Administrative (also called directive) controls are implemented by creating and following organizational policy, procedure, or regulation.
- Technical controls are implemented using software, hardware, or firmware that restricts logical access on an information technology system.
- Physical controls are implemented with physical devices, such as locks, fences, gates, security guards, etc.
Preventive controls prevents actions from occurring.
Detective controls are controls that alert during or after a successful attack.
Corrective controls work by “correcting” a damaged system or process. The corrective access control typically works hand in hand with detective access controls.
After a security incident has occurred, recovery controls may need to be taken in order to restore functionality of the system and organization.
The connection between corrective and recovery controls is important to understand. For example, let us say a user downloads a Trojan horse. A corrective control may be the antivirus software “quarantine.” If the quarantine does not correct the problem, then a recovery control may be implemented to reload software and rebuild the compromised system.
Deterrent controls deter users from performing actions on a system. Examples include a “beware of dog” sign:
A compensating control is an additional security control put in place to compensate for weaknesses in other controls.
Here are more clear-cut examples:
Preventive
- Physical: Lock, mantrap.
- Technical: Firewall.
- Administrative: Pre-employment drug screening.
Detective
- Physical: CCTV, light (used to see an intruder).
- Technical: IDS.
- Administrative: Post-employment random drug tests.
Deterrent
- Physical: “Beware of dog” sign, light (deterring a physical attack).
- Administrative: Sanction policy.
Authentication methods
A key concept for implementing any type of access control is controlling the proper authentication of subjects within the IT system.
There are three basic authentication methods:
- something you know – requires testing the subject with some sort of challenge and response where the subject must respond with a knowledgeable answer.
- something you have – requires that users posses something, such as a token, which proves they are an authenticated user.
- something you are – is biometrics, which uses physical characteristics as a means of identification or authentication.
- A fourth type of authentication is some place you are – describes location-based access control using technologies such as the GPS, IP address-based geo location. these controls can deny access if the subject is in incorrect location.
Biometric Enrollment and Throughput
Enrollment describes the process of registering with a biometric system: creating an account for the first time.
Throughput describes the process of authenticating to a biometric system.
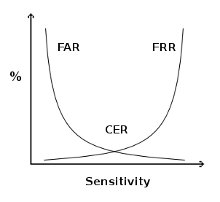
Three metrics are used to judge biometric accuracy:
- the False Reject Rate (FRR) or Type I error- a false rejection occurs when an authorized subject is rejected by the biometric system as unauthorized.
- the False Accept Rate (FAR) or Type II error- a false acceptance occurs when an unauthorized subject is accepted as valid.
- the Crossover Error Rate (CER) – describes the point where the False Reject Rate (FRR) and False Accept Rate (FAR) are equal. CER is also known as the Equal Error Rate (EER). The Crossover Error Rate describes the overall accuracy of a biometric system.
Types of biometric control
Fingerprints are the most widely used biometric control available today.
A retina scan is a laser scan of the capillaries which feed the retina of the back of the eye.
An iris scan is a passive biometric control. A camera takes a picture of the iris (the colored portion of the eye) and then compares photos within the authentication database.
In hand geometry biometric control, measurements are taken from specific points on the subject’s hand: “The devices use a simple concept of measuring and recording the length, width, thickness, and surface area of an individual’s hand while guided on a plate.”
Keyboard dynamics refers to how hard a person presses each key and the rhythm by which the keys are pressed.
Dynamic signatures measure the process by which someone signs his/her name. This process is similar to keyboard dynamics, except that this method measures the handwriting of the subjects while they sign their name.
A voice print measures the subject’s tone of voice while stating a specific sentence or phrase. This type of access control is vulnerable to replay attacks (replaying a recorded voice), so other access controls must be implemented along with the voice print.
Facial scan technology has greatly improved over the last few years. Facial scanning (also called facial recognition) is the process of passively taking a picture of a subject’s face and comparing that picture to a list stored in a database.
Access control technologies
There are several technologies used for the implementation of access control.
Single Sign-On (SSO) allows multiple systems to use a central authentication server (AS). This allows users to authenticate once, and then access multiple, different systems.
SSO is an important access control and can offer the following benefits:
- Improved user productivity.
- Improved developer productivity – SSO provides developers with a common authentication framework.
- Simplified administration.
The disadvantages of SSO are listed below and must be considered before implementing SSO on a system:
- Difficult to retrofit.
- Unattended desktop. For example a malicious user could gain access to user’s resources if the user walks away from his machine and leaves in log in.
- Single point of attack .
SSO is commonly implemented by third-party ticket-based solutions including Kerberos, SESAME or KryptoKnight.
Kerberos is a third-party authentication service that may be used to support Single Sign-On. Kerberos uses secret key encryption and provides mutual authentication of both clients and servers. It protects against network sniffing and replay attacks.
Kerberos has the following components:
- Principal: Client (user) or service
- Realm: A logical Kerberos network
- Ticket: Data that authenticates a principal’s identity
- Credentials: a ticket and a service key
- KDC: Key Distribution Center, which authenticates principals
- TGS: Ticket Granting Service
- TGT: Ticket Granting Ticket
- C/S: Client Server, regarding communications between the two
Kerberos provides mutual authentication of client and server.Kerberos mitigates replay attacks (where attackers sniff Kerberos credentials and replay them on the network) via the use of timestamps.
The primary weakness of Kerberos is that the KDC stores the plaintext keys of all principals (clients and servers). A compromise of the KDC (physical or electronic) can lead to the compromise of every key in the Kerberos realm. The KDC and TGS are also single points of failure.
SESAME is Secure European System for Applications in a Multi-vendor Environment, a single sign-on system that supports heterogeneous environments.
“SESAME adds to Kerberos: heterogeneity, sophisticated access control features, scalability of public key systems, better manageability, audit and delegation.”20 Of those improvements, the addition of public key (asymmetric) encryption is the most compelling. It addresses one of the biggest weaknesses in Kerberos: the plaintext storage of symmetric keys.
Assessing access control
A number of processes exist to assess the effectiveness of access control. Tests with a narrower scope include penetration tests, vulnerability assessments, and security audits.
Penetration tests
Penetration tests may include the following tests:
- Network (Internet)
- Network (internal or DMZ)
- Wardialing
- Wireless
- Physical (attempt to gain entrance into a facility or room)
A zero-knowledge (also called black box) test is “blind”; the penetration tester begins with no external or trusted information, and begins the attack with public information only.
A full-knowledge test (also called crystal-box) provides internal information to the penetration tester, including network diagrams, policies and procedures, and sometimes reports from previous penetration testers.
Penetration testers use the following methodology:
- Planning
- Reconnaissance
- Scanning (also called enumeration)
- Vulnerability assessment
- Exploitation
- Reporting
Vulnerability testing
Vulnerability scanning (also called vulnerability testing) scans a network or system for a list of predefined vulnerabilities such as system misconfiguration, outdated software, or a lack of patching. A vulnerability testing tool such as Nessus (http://www.nessus.org) or OpenVAS (http://www.openvas.org) may be used to identify the vulnerabilities.
Security audit
A security audit is a test against a published standard. Organizations may be audited for PCI (Payment Card Industry) compliance, for example. PCI includes many required controls, such as firewalls, specific access control models, and wireless encryption.
Security assessments
Security assessments view many controls across multiple domains, and may include the following:
- Policies, procedures, and other administrative controls
- Assessing the real world-effectiveness of administrative controls
- Change management
- Architectural review
- Penetration tests
- Vulnerability assessments
- Security audits
You must be logged in to post a comment.