These are my notes of OWASP Belgium Chapter meeting of 19th of March.
KRACKing WPA2 in Practice Using Key Reinstallation Attacks (by Mathy Vanhoef)
This talk subject was about the attack on the WPA2 protocol that was made the (security) headlines last year.  The original paper can be found here and the slides can be found here.
The original paper can be found here and the slides can be found here.
The talk had 4 parts :
- presentation of the attack.
- practical impact
- common misconceptions
- lesson learned
Presentation of the attack
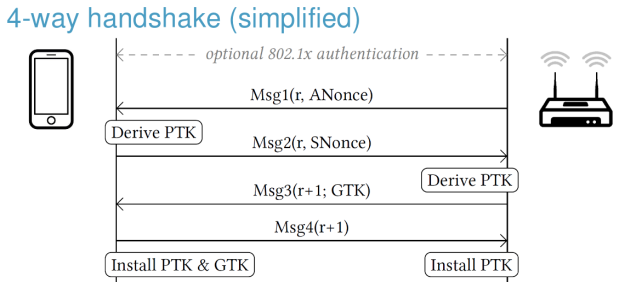
The 4-way handshake is used in any WPA2 protected network. His use if for mutual authentication and to negotiate a new pairwise temporal key (PTK).
The messages sent between the client and the access point (AP) are the following ones:
The PTK is computed in the following way: PTK = Combine (shared secret, ANonce, SNonce) where ANonce, SNonce are random numbers.
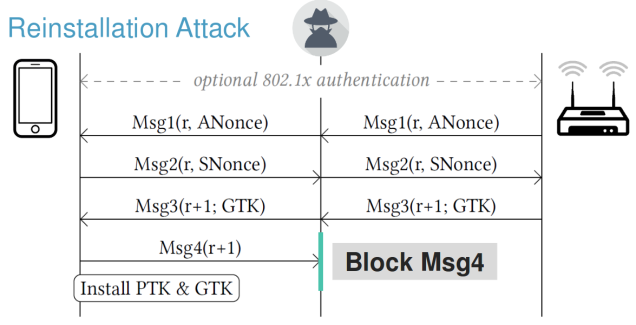
Re-installation attack:
- the attacker will clone the access point on different channel.
- the attacker will/can forward or block frames.
- the first 3 messages are sent back to client and AP.
- message 4 is not sent to the AP; the attacker block this, and the client install the PTK (as per protocol specification)
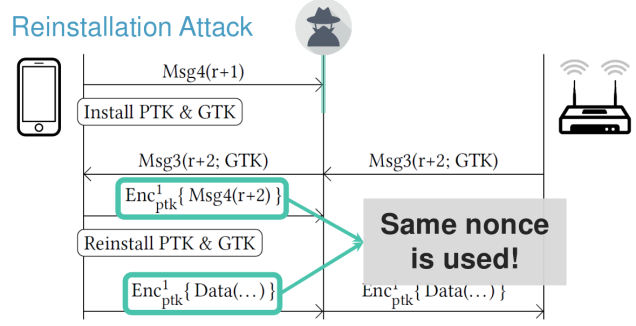
- client can sent encrypted data but the AP will try to recover from this by re-sending message 3.
- then the client will reinstall the PTK meaning that will reset the nonce used to send encrypted data.
- the effect of this key re-installation is that the attacker can decrypt the frames sent by the client.
Other types of handshake protocols are vulnerable to this kind of attack:
- group key handshake.
- fp handshake.
Practical impact of the attack
The main impact is that the attacker can decrypt the data frames sent by the victim to the AP (access point) and the attacker can replay frames sent to the victim.
- iOS 10 and Windows, the 4-way handshake is not affected (because they are not following the WPA2 specification), but the group key handshake is affected.
- Linux and Android 6.0+ that are using the wpa_supplicant 2.4+ version are exposed to install all-zero key vulnerability. The basic explanation of the vulnerability is the following one; the application do not keep the key, the PTK is installed at the kernel level and the application will zeroed the memory buffer that contains the key. But when the key re-installation is triggered, then the all-zero key will be sent to the kernel to be installed.
Countermeasures:
- AP (access point) can prevent most of the attacks on clients:
-
Don’t retransmit message 3/4.
- Don’t retransmit group message 1/2.
-
Common missconceptions
- update only the client or AP is sufficient.
-
in fact both vulnerable clients & vulnerable APs must apply patches
-
- must be connected to network as attacker.
- in fact the attacker only need to be nearby victim and network.
Lessons learned
Making the web secure by design (by Glenn Ten Cate and Riccardo Ten Cate)
- (secure) code examples in more languages; at least Go and Java languages was added since last time I looked.
- the SKF security requirements are mapped directly from the OWASP Application Security Verification Standard (ASVS) project.
- the checklist functionality contains also the OWASP Mobile Application Security Verification Standard (MASVS).
You must be logged in to post a comment.