Ainsi que mentionne dans le chapitre introductif, le processus d’investigation numérique peut être décomposé en trois catégories d’activités: l’acquisition, l’analyse et la présentation. La présentation de l’état de l’art des outils d’investigation numérique sera organisée autour des ces trois catégories, en distinguant entre l’état de l’art des outils d’acquisition des données et l’état de l’art des outils d’analyse et de présentation des données.
Les outils d’acquisition des données permettent d’examiner et ensuite de stocker les données dans des containers de données conçus spécialement pour l’investigation numérique. Un paragraphe sera réservé à la présentation de ces containers des données.
Les containers des données
En général, les containers de données présentes certaines fonctionnalités supplémentaires par rapport à une image brute (RAW). Ces fonctionnalités supplémentaires peuvent concerner la vérification de la cohérence interne, la compression, le cryptage.
En revanche, le format d’image RAW est essentiellement une copie bit à bit des données brutes d’un disque et ne permet pas en général de stocker des métadonnées. Cependant, il arrive que certains outils stockent les métadonnées dans des fichiers secondaires. Le format RAW a été à l’origine utilisé par l’outil Unix dd, mais il est pris en charge par la plupart des applications faisant de l’investigation numérique.
Les formats ouverts
AFF (Advanced Forensic Format)
AFF [AFF] est un format de fichier ouvert et extensible pour stocker des images de disques et des métadonnées associées. En utilisant AFF, l’utilisateur n’est pas dépendent d’un format propriétaire qui peut limiter la façon dont il ou elle peut mener son travail.
Un standard ouvert permet aux enquêteurs d’utiliser rapidement et efficacement leurs outils préférés pour recueillir des renseignements ou résoudre les incidents de sécurité.
AFF offre un design extensible et flexible :
- Design extensible. AFF prend en charge la définition des métadonnées arbitraires en stockant toutes les données sous forme de noms et de paires de valeurs, appelés segments. Certains segments stockent des données du disque et d’autres stockent des métadonnées. En raison de cette conception générale, toutes les métadonnées peuvent être définies en créant simplement un nouveau nom et une paire de valeurs. Chacun des segments peut être comprimé afin de réduire la taille des images et des valeurs de hachages cryptographiques peuvent être calculées pour chaque segment pour assurer l’intégrité des données.
- Design flexible. Pour plus de flexibilité, il existe trois variantes de fichiers AFF – AFF, AFD et AFM et des outils librement disponibles pour convertir facilement les fichiers d’un format a l’autre. Le format original AFF est représenté par un seul fichier, contenant des segments avec les données du disque et des métadonnées. Son contenu peut être compressé, mais il peut être assez grand puisque les données des disques durs modernes atteignent souvent 100 Go en taille. Pour faciliter le transfert, les fichiers AFF peuvent être divisés en plusieurs fichiers au format AFD. Les fichiers AFD (qui ont une taille plus reduite) peuvent être facilement manipulés sur des supports qui limitent la taille de fichiers à 2 Go, tel que par exemple le système de fichiers FAT ou DVD. Le format AFM stocke les métadonnées dans un fichier AFF et les données du disque dans un fichier séparé brut (RAW file). Ce format permet à des outils d’analyse qui prennent en charge le format RAW d’accéder aux données, mais sans perdre les métadonnées.
AFF prend en charge deux algorithmes de compression : zlib, qui est rapide et raisonnablement efficace et LZMA, qui est plus lent, mais beaucoup plus efficace. Zlib est en effet le même algorithme de compression utilisé par EnCase. En conséquence, les fichiers AFF compressés avec zlib ont à peu près la même taille que les fichiers EnCase équivalents. Les fichiers AFF peuvent être re-comprimés en utilisant l’algorithme LZMA.
AFF2.0 supporte le chiffrement des images disque. Les images cryptées ne peuvent pas être accessibles sans la clé de déchiffrement nécessaire.
AFF4
AFF4 est une refonte complète du format AFF. AFF4 est orientée vers des corpus des images très grandes. AFF4 a une architecture orientée objet, tous les objets étant adressables par leur nom qui est unique. AFF4 définit un volume comme un mécanisme de stockage qui peut stocker un segment (bits de données binaires) par son nom et le récupérer aussi par le nom. Actuellement AFF4 a deux implémentations de volume: un répertoire et un fichier Zip.
L’implémentation du volume AFF4 sur un répertoire permet de stocker les segments sous forme de fichiers plats à l’intérieur d’un répertoire régulier sur le système de fichiers. Ceci est vraiment utile si l’on veut faire une image d’un système de fichiers FAT. Il est aussi possible de monter le répertoire sur une url http (par exemple, le répertoire commence avec http://somehost/url/). Cela permet d’utiliser l’image directement depuis le web – pas besoin de télécharger le volume entier.
L ‘implémentation du volume AFF4 sur un fichier Zip stocke les segments à l’intérieur d’une archive zip. Si l’archive est trop grand (plus de 4 Go), l’extension Zip64 est utilisée.
Gfzip (Generic Forensic Zip)
Gfzip [GFZIP] vise à fournir un format de fichier ouvert « compressé » et « signé » pour des fichiers d’image disque. Gfzip utilise l’algorithme SHA256 pour vérifier l’intégrité de données au lieu de SHA1 ou MD5. Les métadonnées fournies par l’utilisateur sont incorporées dans une section spéciale dans le fichier. Une autre fonctionnalité importante de gfzip est l’utilisation de données et métadonnées signées avec des certificats x509.
Sgzip
Introduit par le produit PyFlag (un outil pour faire de l’analyse numérique) et démarré comme un projet dans le département de la défense australien, sgzip est une variante du format gzip sur lequel on peut faire des recherches. En comprimant individuellement les blocs de données, sgzip permet de faire des recherches par mots-clés sur des images sans décompresser l’image entièrement.
Les formats propriétaires
EnCase
EnCase [ENCASE] est peut-être le standard de facto pour les containers de données utilisés dans l’investigation numérique, même si c’est un format propriétaire et complètement fermé. Ce format est largement basé sur le format ASR Data’s Expert Witness Compression Format.
Non seulement le format est compressible, il est également consultable. La compression est effectuée au niveau des blocks et permet de générer et de conserver des pointers vers des fichiers, pour améliorer la vitesse de la consultation. Les images EnCase peuvent être divisées en plusieurs fichiers (par exemple, pour l’archivage sur CD ou DVD). Le format restreint le type et la quantité des métadonnées qui peuvent être associés à une image.
Les formats IDIF, IRBF, IEIF de ILook
La société ILook [ILOOK] offre trois formats d’image propriétaires : un format comprimé (IDIF), un format non-compressé (IRBF) et un format crypté (IEIF). Bien que peu de détails techniques soient divulgués publiquement, la documentation en ligne fournit quelques indications: IDIF a un support pour «la journalisation des actions de l’utilisateur”. IRBF est semblable à IDIF, sauf que les images de disque ne sont pas compressées; IEIF, quant à lui, chiffre lesdites images. Les outils d’ILook permet la transformation de chacun de ces formats en format brut (RAW files).
Il y d’autres formats propriétaires moins connues comme ProDiscover, RAID (Rapid Action Imaging Device), SMART. Le tableau suivant récapitule les principales caractéristiques des différents formats des containers des données.
| Extensible (supporte le stockage demétadonnéesarbitraire) | Non-Propriétaire | Compressé & recherchable | |
| AFF | X | X | X |
| EnCase | X | ||
| ILook | ? | X | |
| Gfzip | X | ||
| Sgzip | X | X | |
| SMART | X | ||
| ProDiscover | X | X |
Les principales caractéristiques des différents formats de fichiers
Les outils d’acquisition des données
Dans la création d’une image numérique d’un disque d’un système d’information, on essaye de capturer une représentation aussi exacte que possible du média source. Un bon procédé de copie d’image, génère un duplicate exacte du média source en cours d’investigation. Par duplicate exacte on comprend une copie octet par octet du support original. Le processus de création d’une image numérique ne devrait pas modifier le support d’origine, il devrait parvenir à acquérir entièrement les données du média d’origine et ne pas introduire dans l’image crée des données qui ne sont pas présents sur le média source.
Travailler avec des preuves numériques d’origine peut être très dangereux parce que l’original peut être modifié ou détruit avec une relative facilité. En accédant les medias d’origine seulement une fois, pour générer la copie numérique, nous minimisons les possibilités de modifier l’original accidentellement. Un autre avantage de travailler sur une copie est qu’en cas de modification par erreur de la copie d’image, on peut générer un duplicata exact du support d’origine.
Une autre raison d’utiliser des outils d’acquisition des données est leur capacité a fournir des informations exhaustives. L’examen d’un système de fichiers tel que présenté par le système d’exploitation n’est pas suffisant pour un processus d’investigation numérique. La plupart des volumes contiennent des données potentiellement intéressantes qui ne sont pas visibles ; on peut appeler ces données, des “données supprimées”. Il y en a plusieurs catégories de “données supprimées” :
- Les fichiers supprimés sont “les plus récupérables.” En général, cela se réfère à des fichiers qui ont été effacés de façon logique du disque; le fichier n’est plus présent lorsque l’utilisateur consulte un répertoire ; le nom du fichier, la structure des métadonnées et les données du fichier sont marqués comme «libres». Cependant, les connexions entre le nom du ficher, les métadonnées respectives et le contenu du fichier sont encore intactes et la récupération du fichier consiste à enregistrer le nom du fichier et des structures pertinentes de métadonnées, puis d’extraire son contenu.
- Les fichiers orphelins sont similaires à des fichiers supprimés à l’exception du lien entre le nom du fichier et les métadonnées qui n’est plus exact. Dans ce cas, la récupération de données et des métadonnées est encore possible, mais il n’y a pas de corrélation directe entre le nom du fichier et les données récupérées.
- Les fichiers non affectés sont les fichiers qui ont été supprimés et leurs noms et ou métadonnées ont été réutilisés par d ‘autres fichiers. Dans ce cas, le seul moyen de récupérer les informations est par l’utilisation du « data carving ». Seules les informations qui n’ont pas été allouées a d’autres fichiers pourront etre recuperees.
- Les fichiers réécrits ce sont les fichiers dont une ou plusieurs de leurs unités de données ont ete réaffectées à un autre fichier. Le rétablissement complet n’est plus possible, mais la reprise partielle peut dépendre de la mesure de l’écrasement.
Matériels
DeepSpar Disk Imager
DiskImager [DEEPSPAR] est une solution matérielle pour faire une copie bit a bit du contenu d’un disque. Les disques source et cible sont connectés a un boitier qui lui même est connecté à un ordinateur. Le boitier est capable de commander le disque source en exécutant des commandes au niveau de l’interface SATA sans passer par des appels BIOS, ce qui facilite la récupération des zones de disque corrompues.
Contrairement aux outils d’investigation numérique, le DiskImager ne crée pas une image du disque source. Au lieu de cela, il utilise des commandes et des techniques pour copier tous les secteurs du disque source directement sur le disque de destination. Le disque de destination peut ensuite être utilisé par n’importe quel logiciel de récupération de données ou d’investigation numérique pour la récupération des données.
D’autres sociétés offrent des produits similaires au DiskImager : PSIClone (http://www.thepsiclone.com/), ICS Solo 3 (http://www.icsforensic.com/)
Logiciels
Volatility
Volatility [VOLATILITY] est une collection d’outils complètement ouverts, développés en Python sous licence GPL, pour l’extraction des données de la mémoire volatile (RAM). L’extraction de données est réalisée complètement indépendemment du système d’exploitation utilisé, mais offre la possibilité d’avoir un aperçu de l’état d’exécution du système.
Volatility fournit actuellement des capacités d’extraction des données concernant les processus en cours, les sockets réseaux ouverts, les connections réseaux ouverts, les fichiers ouverts pour chaque processus, la mémoire adressée par processus, les modules du noyau chargés.
dd (Data Dump)
La commande dd[DD] est l’outil open-source fondamental necessaire pour créer une image d’un disque. Compte tenu du fait qu’il est presque universellement présent sur n’importe quel système d’exploitation Unix, il est la base de plusieurs autres utilitaires d’acquisition des données et l’apprentissage de son fonctionnement est important à n’importe quel examinateur.
L’utilisateur peut fournir des arguments divers et des drapeaux pour modifier ce comportement simple, mais la syntaxe de base de l’outil est assez claire.
Donc, pour faire un simple clone d’un disque à l’autre, il faut utiliser l’outil de la façon suivante:
dd if=/dev/sda of=/dev/sdb bs=4096
La commande lit par tranches de 4096 octets du disque /dev/sda vers le deuxième disque (/dev/sdb).
Le clonage d’un disque est intéressant, mais d’une utilité limitée pour un examinateur. Dans la plupart des cas, nous nous intéressons à la création d’une image numérique d’un fichier qui contient l’ensemble du contenu présent sur le disque source. Cette operation est egalement tres simple à effectuer en utilisant la même syntaxe.
$ dd if=/dev/sdg of=dd.img bs=32K 60832+0 records in60832+0 records out 1993342976 bytes (2.0 GB) copied, 873.939 s, 2.3 MB/s
Les éléments clés d’intérêt dans la sortie de la console pour la commande dd sont les lignes « records in » et « records out ». A ce titre, on peut observer tout d’abord que le nombre d’enregistrements lus et écrits est le même – cela indique qu’il n’y a pas de perte des données en raison d’une défaillance du disque, de l’échec d’écriture du fichier de sortie ou bien, pour toute autre raison.
dcfldd
Le projet dcfldd[DCFLDD] est un projet dérivé du projet dd, donc ses fonctionnalités sont similaires au dd. Toutefois, dcfldd a des capacités intéressantes qui ne se retrouvent pas dans dd. La plupart des fonctionnalités tournent autour de la création des valeurs de hachage, la validation, la journalisation de l’activité et la division du fichier de sortie en plusieurs fichiers de taille fixe. Les fonctions étendues de dcfldd, ainsi que les fonctions de dd peuvent être examinées en passant l’option –help pour la commande dcfldd.
dc3dd
dc3dd[DC3DD] est conçu comme un patch appliqué à GNU dd, plutôt qu’une variante de dd, de sorte que dc3dd est capable d’intégrer les modifications apportées sur dd plus rapidement que dcfldd.
dc3dd produit un journal de hachage à la console ainsi que dans un fichier passé dans l’argument hashlog. En outre, a la fin d’une opération, l’outil présente le nombre de secteurs écrits/lus plutôt que le nombre de blocs.
ewfacquire, ewfacquirestream
Les outils ewfacquire et ewfacquirestream font partie de la bibliothèque libewf [LIBEWF]. Ils peuvent créer des fichiers dans le format EnCase, FTK Imager et SMART. ewfacquire est destiné à lire à partir de périphériques et ewfacquirestream à partir des tuyaux (pipes). Ces deux outils peuvent calculer des valeurs de hachage MD5 quand les données sont en cours d’acquisition.
NED (The Open Source Network Evidence Duplicator)
NED [NED] est un outil d’acquisition et duplication de données plutôt unique dans son genre, puisqu’il utilise un modèle client-serveur. Le serveur stocke les données envoyées pas le client, le serveur et le client en communiquant par le protocole UDP. NED a une architecture ouverte qui accepte des plugins. Les plugins sont des modules qui se branchent dans NED et entendent les fonctionnalités pendant le processus d’acquisition. NED contient déjà les plugins suivants :
- « Image Store Plugin« (crée une image dd du disc client), «Hash« (calcule les empreintes des fichiers acquis)
- « String Search« (la recherche par mots clés)
- « Carv« (pour la recherche des fichiers effacées)
- « Compress Image Store« (comprimer les images acquises)
Malgré des débuts prometteurs, le projet NED est actuellement disparu, la dernière version téléchargeable datant de 2004.
FTK Imager
Le Forensic Toolkit Imager [FTKI] est une suite d’outils d’acquisition des données commercialisées par la société AccessData. FTK Imager est capable de stocker les images de disques le format ECase, SMART, dans le format brut (raw) mais aussi dans le format ISO/CUE.
D’autres outils sont disponibles sur la plateforme Unix/Linux ; Voici une liste non-exhaustive :
| Windows | Unix/Linux | ||
| Adepto | http://www.e-fense.com/helix/ | X | |
| AIR | http://air-imager.sourceforge.net/ | X | |
| EnCase LinEn | http://www.digitalintelligence.com | X | |
| GNU ddrescue | http://www.gnu.org/software/ddrescue | X | |
| dd_rescue | http://www.garloff.de/kurt/linux/ddrescue/ | X | |
| MacQuisition Boot CD | https://www.blackbagtech.com | X | |
| rdd | http://sourceforge.net/projects/rdd | X | |
| GuyManager | http://guymager.sourceforge.net/ | X | |
| ASR Data Acquisition & Analysis, | http://www.asrdata.com/ | X | |
| Paraben Forensics | http://www.paraben-forensics.com/ | X | |
| XWay Forensics | http://www.x-ways.net/forensics/ | X | |
| Forensic Imager | http://www.forensicimager.com/ | X | |
| Forensic Acquisition Utilities | X | ||
| FTTimes | http://ftimes.sourceforge.net/FTimes/index.shtml | X | X |
D’autres outils d’acquisition des données
Les outils d’analyse des données
Le but des outils d’analyse des données est d’identifier, extraire et analyser les artefacts générés par les outils d’acquisition de données. L’identification consiste à déterminer les fichiers actifs ou supprimés, qui sont présents dans un container de données. L’extraction consiste dans la récupération des fichiers et des métadonnées pertinents. L’analyse est le processus d’examen de l’ensemble des données, qui idéalement conduit à des résultats probants.
Gratuit
The Sleuth KIT
TSK [TSK] est une collection d’outils UNIX en ligne de commande permettant de faire de l’investigation numérique. La collection contient une vingtaine d’outils et la majeure partie des outils sont nommés de façon logique, en indiquant la couche du système de fichiers sur laquelle ils opèrent et le type de résultat obtenu.
Les préfixes des noms des outils TSK sont:
- « mm-» pour les outils qui travaillent sur des volumes (media management)
- « fs- » pour les outils qui travaillent sur la structure du système de fichiers
- « blk-» pour les outils qui travaillent sur les blocs des données.
- « i-» pour les outils qui travaillent sur les métadonnées (inodes)
- « f-» pour les outils qui travaillent sur les noms des fichiers
- « j-» pour les outils qui travaillent sur le système de journalisation de système de fichiers.
- « img-» pour les outils qui travaillent sur les images des systèmes de fichiers.
Les suffixes communs trouvés dans les outils TSK qui indiquent la fonction attendue du l’outil
sont les suivants:
- «-stat » affiche des informations générales sur l’élément interrogé ; similaire à la commande “stat” sur les systèmes Unix.
- « -ls » affiche le contenu de l’élément interrogé ; similaire à la commande “ls” sur les systèmes Unix.
- « -cat » extrait le contenu de l’élément interrogé ; similaire à la commande “cat” sur les systèmes Unix.
Autopsy
Autopsy[AUTOPSY] est une interface graphique web pour le The Sleuth Kit.
Scalpel
Scalpel [SCALPEL] est un utilitaire pour faire du carving qui lit une base de données des définitions d’entêtes et des pieds de page (footers) et extrait des fichiers correspondants ou des fragments des fichiers a partir des images des disques ou des fichiers raw. Scalpel est Independent du système des fichiers et est capable de travailler sur des partitions FATx, NTFS, ext2/3, HFS+.
PyFLAG
PyFLAG [PYFLAG] est un outil d’analyse basé sur le langage Python. PyFLAG est une application web, donc un utilisateur n’a besoin que d’un simple navigateur Web pour effectuer un examen.
Étant une application web utilisant une base de données, donne à PyFLAG plusieurs avantages par rapport aux outils traditionnels d’investigation numérique, qui tendent à être utilisés par un seul utilisateur sur un seul système. Une instance PyFLAG peut supporter plusieurs utilisateurs sur un seul cas ou plusieurs utilisateurs travaillant sur des cas différents en parallèle. En plus du modèle de serveur, PyFLAG a quelques autres fonctionnalités qui en font un outil intéressant pour un examinateur en utilisant des outils open source.
PyFLAG dispose d’un système de fichiers unifié virtuel (VFS) pour tous les objets en cours d’examen. PyFLAG se réfère à chacun de ces éléments des inodes. Chaque élément chargé dans la base de données du PyFLAG reçoit un inode PyFLAG, en plus des métadonnées des l’élément. Cela signifie qu’on peut charger sous la même racine virtuelle des images de système de fichiers (quelque soit leur nombre), des captures du trafic réseau, des fichiers de journalisation et même des flux de données non structurées, ces informations pouvant être traitées par la suite traitées avec PyFLAG.
Fiwalk
Fiwalk[FIWALK] est une bibliothèque et une suite de programmes connexes visant à automatiser une grande partie de l’analyse du système de fichiers initial effectué lors d’une investigation numérique. Le nom vient de “file & inode walk», qui décrit les fonctions du programme. La sortie de Fiwalk est une cartographie des systèmes de fichiers d’un disque et les fichiers contenus, y compris les métadonnées de fichiers intégrés. L’objectif du projet Fiwalk est de fournir un langage de description XML normalisé pour le contenu d’un fichier contenant des données forensiques et de permettre un traitement plus rapide des données provenant d’une investigation numérique.
Parce que Fiwalk hérite les capacités d’analyse des systèmes de fichiers de TSK, il est capable de supporter n’importe quelle partition, volume ou structure du système de fichiers que TSK est capable de lire. En plus de sa sortie standard XML, Fiwalk peut fournir une sortie dans un format texte, un format TSK ou un format CSV.
Hachoir
Hachoir [HACHOIR] est un framework générique pour la manipulation de fichiers binaires. Ecrit en Python, il est indépendant du système d’exploitation et il peut accepter beaucoup d’interfaces graphiques utilisateur (ncurses, wxWidget, Gtk +). Bien qu’il contienne quelques fonctions de modification de fichiers, il est normalement prévu pour examiner des fichiers existants en étant capable actuellement de gérer plus d’une soixante des formats de fichiers. La reconnaissance du format de fichier est basée sur les en-têtes et il dispose aussi d’un analyseur tolérant aux défauts, conçu pour gérer les fichiers tronqués ou incomplets.
Hachoir permet de “naviguer” sur tout flux binaire, de la même manière qu’on peut naviguer sur des répertoires et des fichiers. Un fichier est divisé en un arbre de champs, où le plus petit champ est un bit. Il existe d’autres types de champs: des entiers, des chaînes de bits, etc.
Hachoir est composé d’un parseur principal (hachoir-core), des divers parseurs pour différents formats de fichier (hachoir-parser) et d’autres programmes périphériques.
Commercial
Forensics Toolkit
Forensic Toolkit [FTKI] est un outil qui permet de faire une analyse numérique complète. Pour la création des images de disques, FTK contiens le FTK Imager. Pour stocker les informations, FTK utilise une base de données, qui rend le produit accessible par plusieurs utilisateurs en mode concurrent. Le FTK Case Manager permet le stockage des preuves numériques mais aussi l’indexation des preuves.
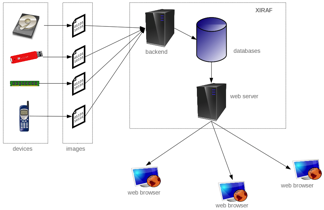
XIRAF
Xiraf [XIRAF] est un outil d’analyse de données. Xiraf indexe et rend consultable les preuves numériques par l’extraction et l’organisation de l’information qui a de la valeur pour les enquêteurs. Xiraf est capable d’indexer des fichiers de métadonnées, des enregistrements d’historique du navigateur, des clés des registres, des propriétés des documents, emails, etc. Une fois que la preuve a été indexée, les enquêteurs recherchent les éléments de preuve à travers l’interface web de XIRAF. Avec cette interface, les enquêteurs peuvent combiner des recherches utilisant des multiples dimensions comme le temps, l’emplacement et le contenu.
Un premier prototype du système a été présenté à DFRWS 2006 dans un document intitulé “XIRAF – XML-based indexing and querying for digital forensics“.
Les défis futurs de l’investigation numérique
L’investigation numérique en est encore à ses balbutiements compte tenu de son existence relativement courte, ainsi que du rythme rapide du changement technologique. Cette situation se traduit par de nombreux défis et controverses avec lesquels les communautés juridiques et judiciaires doivent se débattre. Les défis sont nombreux. Un premier défi est lié à la vitesse de changement des technologies informatiques. Un autre défi est de trouver un consensus au sein de la communauté scientifique pour trouver et établir les bonnes pratiques d’un processus d’investigation numérique.
L’investigation numérique est à l’origine d’une collision entre deux forces apparemment irréductibles: le système juridique d’une coté qui fonctionne à un rythme relativement lent et de l’autre coté la communauté de l’investigation numérique qui est en contact avec la technologie qui avance et évolue a la vitesse de l’éclair.
Du point de vue technologique, l’investigation numérique est confrontée a deux nouvelles technologies qui soulèvent des sérieux défis: l’informatique dans les nouages (cloud computing) et les disques SSD (Solid State Drive). Dans l’état actuel, l’investigation numérique dans un de ces environnements pourrait très bien être irrécupérable pour des raisons soit techniques ou juridiques (ou les deux). Ces technologies sont en usage aujourd’hui et représentent un problème pour lequel il n’existe pas de solution facile.
L’informatique dans les nuages peut être un rêve devenu réalité pour ceux qui travaillent dans l’industrie de l’information, mais cela représente un cauchemar pour ceux qui traitent avec des preuves numériques. Les principaux défis sont de deux ordres, l’un technique et l’autre juridique. Le défi technique est lié a l’impossibilité d’accéder à distance au contenu effacé puisque il y a des fortes chances que le disque qui contenait cette information ait été déjà réutilisé pour stocker un autre contenu. Le défi juridique est lié aux juridictions multiples qui peuvent s’appliquer aux données, aux applications et/ou aux fournisseur de services dans les nouages.
Les mémoires SSD posent un défi technique lié à l’effacement des fichiers. L’écriture d’une cellule d’une mémoire SSD doit passer d’abord par le reset du contenu de la cellule, ce qui diminue fortement les performances en écriture du disc. Pour combler ce manque de performance, les cellules sont resetées lors de l’effacement des fichiers soit par le système de l’exploitation via la commande TRIM, soit directement par le contrôleur du SSD. Donc, lors de l’effacement d’un fichier, le contenu du fichier est complètement perdu, ce qui pose des problèmes lors des investigations numériques.
You must be logged in to post a comment.