Note: This notes were made using the following books: “CISPP Study Guide” and “CISSP for dummies”.
Telecommunications and Network Security employs defense-in-depth, as we do in all 10 domains of the common body of knowledge. Any one control may fail, so multiple controls are always recommended.
Network concepts
Simplex communication is one-way, like a car radio tuned to a music station. Half-duplex communication sends or receives at one time only (not simultaneously), like a walkie-talkie. Full-duplex communications sends and receive simultaneously, like two people having a face-to-face conversation.
Baseband networks have one channel, and can only send one signal at a time. Ethernet networks are baseband: a “100baseT” UTP cable means 100 megabit, baseband, and twisted pair.
Broadband networks have multiple channels and can send multiple signals at a time, like cable TV.
A LAN is a Local Area Network. A LAN is a comparatively small network, typically confined to a building or an area within one. A MAN is a Metropolitan Area Network, which is typically confined to a city, a zip code, a campus, or office park. A WAN is a Wide Area Network, typically covering cities, states, or countries. A GAN is a Global Area Network; a global collection of WANs.
The Internet is a global collection of peered networks running TCP/IP, providing best effort service. An Intranet is a privately owned network running TCP/IP, such as a company network. An Extranet is a connection between private Intranets, such as connections to business partner Intranets.
Circuit-switched networks can provide dedicated bandwidth to point-to-point connections, such as a T1 connecting two offices. One drawback of circuit-switched networks: once a channel or circuit is connected, it is dedicated to that purpose, even while no data is being transferred.
Packet-switched networkswere designed to handle network failures more robustly. Instead of using dedicated circuits, data is broken into packets, each sent individually. If multiple routes are available between two points on a network, packet switching can choose the best route, and fall back to secondary routes in case of failure. Packets may take any path (and different paths) across a network, and are then reassembled by the receiving node.
Packet switched networks may use Quality of Service (QoS) to give specific traffic precedence over other traffic. For example: QoS is often applied to Voice over IP (VoIP) traffic (voice via packet-switched data networks), to avoid interruption of phone calls.
Network models such as OSI and TCP/IP are designed in layers. Each layer performs a specific function, and the complexity of that functionality is contained within its layer. Changes in one layer do not directly affect another.
A network model is a description of how a network protocol suite operates, such as the OSI Model or TCP/IP Model. A network stack is a network protocol suite programmed in software or hardware.
Network models
The ISO OSI reference model
The OSI (Open System Interconnection) Reference Model is a layered network model. The model is abstract: we do not directly run the OSI model in our systems.
The OSI model has seven layers. The layers may be listed in top-to-bottom or bottom-to-top order. Using the latter, they are Physical, Data Link, Network, Transport, Session, Presentation, and Application.
The physical layer describes units of data such as bits represented by energy (such as light, electricity, or radio waves) and the medium used to carry them (such as copper or fiber optic cables). WLANs have a physical layer, even though we cannot physically touch it. Layer 1 devices include hubs and repeaters.
The Data Link layer handles access to the physical layer as well as local area network communication. An Ethernet card and its MAC (Media Access Control) address are at Layer 2, as are switches and bridges. Layer 2 is divided into two sub-layers: Media Access Control (MAC) and Logical Link Control (LLC).
The Network layer describes routing: moving data from a system on one LAN to a system on another. IP addresses and routers exist at Layer 3.
The Transport layer handles packet sequencing, flow control, and error detection. TCP and UDP are Layer 4 protocols.
The Session layer manages sessions, which provide maintenance on connections.A good way to remember the session layer’s function is “connections between applications.” The Session Layer uses simplex, half-duplex, and full-duplex communication.
The Presentation layer presents data to the application (and user) in a comprehensible way.
The Application layer is where you interface with your computer application.
Try creating a mnemonic to recall the layers of he OSI model, such as : Please Do Not Throw Sausage Pizza Away or Adult People Should Try New Dairy Products.
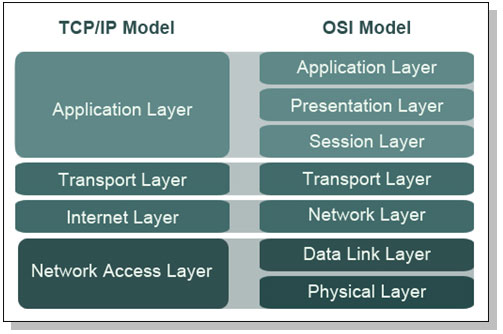
The TCP/IP model
TCP/IP is an informal name, the formal name is Internet Protocol Suite. The TCP/IP model is simpler that ISO/OSI.
The Network Access Layer of the TCP/IP model combines layers 1 (Physical) and 2 (Data Link) of the OSI model.
The Internet Layer of the TCP/IP model aligns with the Layer 3 (Network) layer of the OSI model. This is where IP addresses and routing live.
The Host-to-Host Transport Layer (sometimes called either “Host-to-Host” or, more commonly, “Transport” alone.It is where applications are addressed on a network, via ports. TCP and UDP are the two Transport Layer protocols of TCP/IP.
The TCP/IP Application Layer combines Layers 5 though 7 (Session, Presentation, and Application) of the OSI model. Most of these protocols use a client-server architecture, where a client (such as ssh) connects to a listening server (called a daemon on UNIX systems) such as sshd.
Here is the mapping between ISO/OSI model and TCP/IP model:
Encapsulation takes information from a higher layer and adds a header to it, treating the higher layer information as data.For example, as the data moves down the stack in the TCP/IP model, application layer data is encapsulated in a layer 4 TCP segment. That TCP segment is encapsulated in a Layer 3 IP packet. That IP packet is encapsulated in a Layer 2 Ethernet frame. The frame is then converted into bits at Layer 1 and sent across the local network.
Data, segments, packets, frames, and bits are examples of Protocol Data Units (PDUs).
Physical Layer Protocols and concepts
LAN Physical Network Technologies
- Bus – All devices are connected to a single cable that’s terminated on both ends. Each node inspects the data as it passes along the bus. Network buses are fragile; should the network cable beak anywhere along the bus, the entire bus will go down.
- Tree – A tree is also called hierarchical network: a network with a root node, and branch nodes that are at least three levels deep (two levels would make it a star).
- Ring – A physical ring connects network nodes in a ring: if you follow the cable from node to node, you will finish where you began. In the ring topology, all communication ravels in a single direction around the ring.
- Star – Each node is connected directly to a central device such as a hub or a switch. Star topology has become the dominant physical topology for LANs.
- Mesh – All systems are interconnected to provide multiple path to all other resources. In most networks a partial mesh is implemented for only the most critical networks components, such as routers, switches and servers. Meshes heave superior availability and are often used for highly available (HA) server clusters.
Cable and connector types
Cables carry the electrical or light signals that represents data, between devices on a network.Fundamental network cabling terms to understand include EMI, noise, crosstalk, and attenuation.
Electro Magnetic Interference (EMI) is interference caused by magnetism created by electricity. Crosstalk occurs when a signal crosses from one cable to another. Attenuation is the weakening of signal as it travels further from the source.
- Coaxial cable – consists of single, solid copper-wire-core, surrounded by a plastic insulator, braided-metal shielding, all covered with a plastic sheath. This construction makes the cable very durable and resistant to EMI and Radio Frequency Interference (RFI) signals. Coaxial cables comes in 2 flavors: thick and thin.
- Twinaxial cable – very similar to coax cables, but it consists of two solid copper-wire cores, rather that a single one. Twinax ix used to achieve hight data (10 Gb) transmission speed over very short distances (10 meter).
- Twisted-pair cable are classified by categories according to rated speed. Tighter twisting results in more dampening: a Category 6 designed for gigabit networking have far twitter twisting than a Category 3 fast Ethernet cable.
| Category | Speed | Use |
|---|---|---|
| 1 | 1 Mbps | Voice Only (Telephone Wire) |
| 2 | 4 Mbps | LocalTalk & Telephone (Rarely used) |
| 3 | 16 Mbps | 10BaseT Ethernet |
| 4 | 20 Mbps | Token Ring (Rarely used) |
| 5 | 100 Mbps (2 pair) | 100BaseT Ethernet |
| 1000 Mbps (4 pair) | Gigabit Ethernet | |
| 5e | 1,000 Mbps | Gigabit Ethernet |
| 6 | 10,000 Mbps | Gigabit Ethernet |
- Fiber-optic cable – Fiber Optic network cable (simply called “fiber”) uses light to carry information, which can carry a tremendous amount of information. Fiber can be used to transmit via long distances: past 50 miles, much further than any copper cable. Fiber’s advantages are speed, distance, and immunity to EMI. Disadvantages include cost and complexity.
Network equipement
- Network Interface Cards (NIC) are used to connect a computer to the network.
- Repeater – is a non intelligent device that simply amplifies a signal.A repeater receives bits on one port, and “repeats” them out the other port. The repeater has no understanding of protocols; it simply repeats bits.
- Hub– A hub is a repeater with more than two ports. It receives bits on one port and repeats them across all other ports.Hubs provide no traffic isolation and have no security: all nodes see all traffic sent by the hub.Hubs are also half-duplex devices: they cannot send and receive simultaneously.Hubs also have one “collision domain”: any node may send colliding traffic with another.
Data Link Layer Protocols and concepts
LAN protocols and transmission methods
Common LAN protocols defines at the Layer 2 level are :
- Ethernet – is a dominant local area networking technology that transmits network data via frames. It originally used a physical bus topology, but later added support for physical star. Carrier Sense Multiple Access (CSMA) is designed to address collisions.CSMA/CD is used for systems that can send and receive simultaneously, such as wired Ethernet. CSMA/CA (Collision Avoidance) is used for systems such as 802.11 wireless that cannot send and receive simultaneously.
- ARCNet (Attached Resource Computer Network) – is one of the earliest LAN technology. It is implemented in the star topology by using the coaxial cable.
- Token-Ring – like ARCNet, the Token Ring is a legacy LAN technologies. Both pass network traffic via tokens. Possession of a token allows a node to read or write traffic on a network. This solves the collision issue faced by Ethernet: nodes cannot transmit without a token.
- FDDI (Fiber Distributed Data Interface) – is another legacy LAN technology, running a logical network ring via a primary and secondary counter-rotating fiber optic ring.
- ARP (Address Resolution Protocol) – is used to translate between Layer 2 MAC addresses and Layer 3 IP addresses. ARP discovers physical addresses of attached devices by broadcasting ARP query messages on the network segment. IP-address-to-MAC-address translations are then maintained in a dynamic table. ARP maps an IP address to a MAC address and is used to identify a device’s hardware address when only the IP address is known.
- RARP (Reverse Address Resolution Protocol) – is used by diskless workstations to request an IP address. The system broadcasts a RARP message that that provides the system MAC address and request to be informed of its IP address. RARP maps between a MAC address to an IP address and is used to identify a device’s IP address when only the MAC address is known.
LAN data transmissions are classified as :
- Unicast – is one-to-one traffic, such as a client surfing the Web.
- Multicast – Packets are copied and sent from the source to multiple destination devices by using a special multicast IP address.
- Broadcast traffic is sent to all stations on a LAN. There are two types of IPv4 broadcast addresses: limited broadcast and directed broadcast. The limited broadcast address is 255.255.255.255. It is “limited” because it is never forwarded across a router, unlike a directed broadcast.
WLAN protocols and transmission methods
Wireless Local Area Networks (WLANs) transmit information via electromagnetic waves (such as radio) or light.
The most common form of wireless data networking is the 802.11 wireless standard, and the first 802.11 standard with reasonable security is 802.11i.
| Protocol | Release Date | Op. Frequency | Data Rate (Typical) | Data Rate (Max) | Range (Indoor) |
| Legacy | 1997 | 2.4 -2.5 GHz | 1 Mbit/s | 2 Mbit/s | ? |
| 802.11a | 1999 | 5.15-5.35/5.47-5.725/5.725-5.875 GHz | 25 Mbit/s | 54 Mbit/s | ~30 meters (~100 feet) |
| 802.11b | 1999 | 2.4-2.5 GHz | 6.5 Mbit/s | 11 Mbit/s | ~50 meters (~150 feet) |
| 802.11g | 2003 | 2.4-2.5 GHz | 11 Mbit/s | 54 Mbit/s | ~30 meters (~100 feet) |
| 802.11n | 2006 (draft) | 2.4 GHz or 5 GHz bands | 200 Mbit/s | 540 Mbit/s | ~50 meters (~160 feet) |
Another WLAN standard is IEEE standard 802.15 a.k.a Bluetooth. Bluetooth, is a Personal Area Network (PAN) wireless technology, operating in the same 2.4 GHz frequency as many types of 802.11 wireless. Sensitive devices should disable automatic discovery by other Bluetooth devices. The “security” of the discovery relies on the secrecy of the 48-bit MAC address of the Bluetooth adapter. Even when disabled, the Bluetooth devices can be discovered by guessing the MAC address.
WAN technologies and protocols
WAN protocols define how frames are carried across a single data link between two devices.
Point-to-point links – these links provide a single, pre-establish WAN communications path from the customer network, to a remote network.
- SLIP (Serial Line IP) – was originally developed to support TCP?IP networking over low-speed asynchronous serial lines.
- PPP (Pont-to-Point protocol) – the successor of SLIP, provides router-to-router and host-to-network connections over synchronous and asynchronous circuits. PPP adds confidentiality, integrity and authentication via point-to-point links.
- PPTP (Point-to-Point Tunneling Protocol) – tunnels PPP via IP. PPTP doesn’t provides encryption or confidentiality, instead relying on other protocols such as PAP, CHAP and EAP, for security.
- L2F (Layer 2 Forwarding Protocol) – a tunneling protocol developed by Cisco and used to implement VPNs.
Circuit-switched networks – a dedicated physical circuit path is established, maintained and terminated between the sender and receiver across a carrier network for each communications session. This network type is used extensively in telephone company networks.
- xDSL (Digital Subscriber Line) – uses existing analog phones lines to deliver high-bandwith connectivity ti remote customers.
- DOCSIS (Data Over Cable Services Interface Specifications) – is a communication protocol for transmitting high speed data over an existing cable TV system.
- ISDN (Integrated Services Digital Network) – is a communication protocol that operates over analog phone lines that have been converted to use digital signaling.
Packet-switched networks – devices share bandwidth on communications links to transport packets between a sender and receiver across a carrier network. This type of network is more resilient to errors and congestions than circuit-switched networks.
- Frame Relay – protocol that provides no error recovery and focuses on speed.
- X.25 – provided a cost-effective way to transmit data over long distances in the 1970s though 1990s.
- ATM (Asynchronous Transfer Mode) – is a WAN technology that uses fixed length cels.ATM cells are 53 bytes long with a 5-bytes header and 48-bytes data portion.
Network equipement
Bridges and switches are Layer 2 devices.
A bridge has two ports, and connects network segments together. Each segment typically has multiple nodes, and the bridge learns the MAC addresses of nodes on either side.Traffic sent from two nodes on the same side of the bridge will not be forwarded across the bridge. Traffic sent from a node on one side of the bridge to the other side will forward across.A bridge has two collision domains.
A switch is a bridge with more than two ports. Also, it is best practice to only connect one device per switch port. Otherwise, everything that is true about a bridge is also true about a switch.A switch shrinks the collision domain to a single port. You will normally have no collisions assuming one device is connected per port (which is best practice). Additionally a switch can be used to implement virtual LANs, which logically segregate a network and limit broadcast domains.
Since switches provide traffic isolation, a Networked Intrusion Detection System (NIDS) connected to a 24-port switch will not see unicast traffic sent to and from other devices on the same switch.
Configuring a Switched Port Analyzer(SPAN) port is one way to solve this problem, by mirroring traffic from multiple switch ports to one “SPAN port.” SPAN is a Cisco term; HP switches use the term “Mirror port.” One drawback to using a switch SPAN port is port bandwidth overload.
A TAP (Test Access Port) provides a way to “tap” into network traffic, and see all unicast streams on a network. Taps are the preferred way to provide promiscuous network access to a sniffer or NIDS.
You must be logged in to post a comment.